Züs Security
Own and control your data with unmatched security and privacy
Prevent Hacks and Breaches at Server with Data Distribution and Split-Keys. Prevent Ransomware at Client with Split-Keys.
Prevent Hacks and Breaches at Server with Data Distribution and Split-Keys. Prevent Ransomware at Client with Split-Keys.
Recently discovered pitfalls of Encryption Encryption ≠ Security 1, 2

Attackers can inject malicious keys into the encryption process

Attackers can force protocol downgrades, preventing encryption

Allows malicious servers to intercept & replace encryption keys

Files are renamed or relocated maliciously, leading to data loss

Attackers can modify or replace data chunks without detection

Attackers insert malicious files & folders leading to data breach

Attackers modify encrypted files undetected, corrupting data

Embedding passwords in shared links are intercepted
The master key is anchored on the blockchain, ensuring a unique and verifiable ID.
Enterprise securely stores master key in zVault, generating Split Keys for operational use.
Split Key is in all Clients and Servers making the master private key impenetrable to internal and external breach.
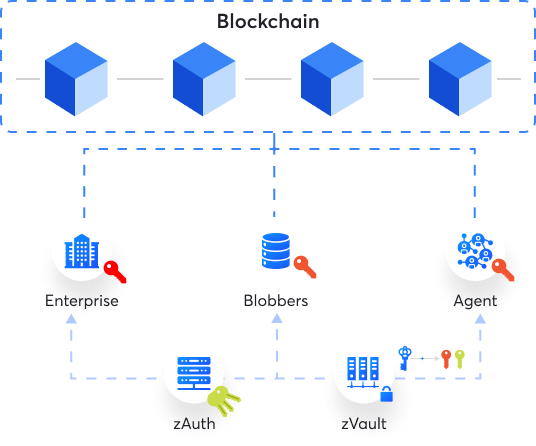
Data contract between Client and Servers is recorded on the blockchain.
& Public Encrypted Sharing
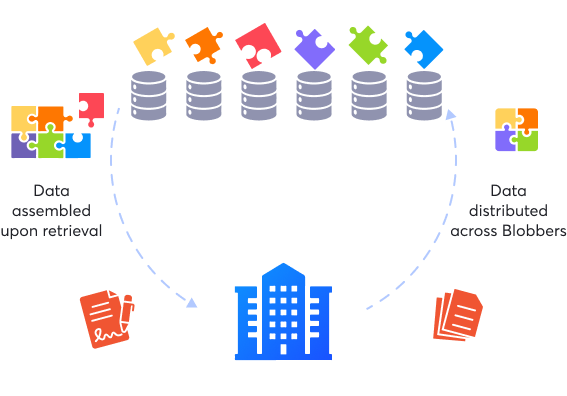
Data is encoded with user defined redundancy and distributed among Blobbers.
Data privacy and availability is not compromised with the hack of servers.
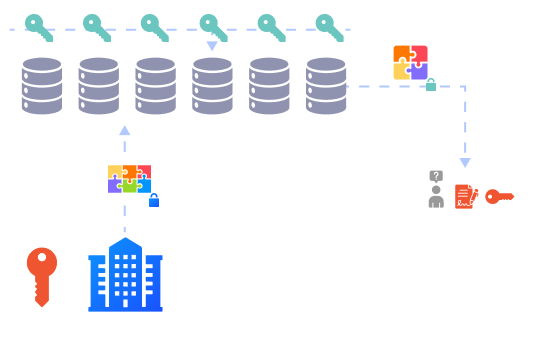
Enterprise generates Proxy Key when sharing encrypted data based on Client's Private Key and Recipient's Public Key. Proxy Key is distributed to servers.
Blobbers use the Proxy Key to re-encrypt the data and can only be decrypted by the Recipient's Private Key.
Easily share an authentication link publicly for convenience—no secure connection required.
An update to the CrowdStrike agent led to a widespread IT outage, impacting millions of Windows devices. Most of the backup images used BitLocker encryption, but the encryption key was stored in a Windows server affected by the outage and so it prevented recovery.
When Züs is used for backups, Windows users gain full ownership and control of their encryption key, since it's managed through a public blockchain network. Moreover, because the data is inherently distributed and encoded across multiple data centers, the backup image does not need to be re-encrypted to restore devices, simplifying recovery without compromising security.
In February 2024, Change Healthcare, a major operator of health payment processing in the US, was hit by a ransomware attack, where the hackers used malware to encrypt the company's systems, preventing access.
If the data is on Zus, it will be distributed over multiple data centers which will make it hard for the attacker to infect all the servers, since they would need to attack the IT operator of each server and try to phish them into installing the malware.
Other related terms: Spoofing, Hijacking, Eavesdropping, and Phishing. In 2017, Equifax data breach exposed over 143 million Americans. The issue was that the website used a shared SSL for hosting—with thousands of other websites using the same certificate. DNS (through fake websites) and SSL spoofing took place to redirect users to a phony website to intercept data from the site.
If Zus storage is used for hosting, the traffic is protected and the man in the middle does not have enough information to reconstruct the content, since data is stored in fragments across multiple datacenter servers.
The SolarWinds hack, also known as the SolarWinds supply chain attack, when the attackers inserted malicious code into SolarWinds' software platform, which was distributed to approximately 18,000 customers through routine updates. The malicious code, known as SUNBURST, created a backdoor in the infected systems.
This allowed the attackers to install additional malware and exfiltrate data without being detected for an extended period of time. The attackers used obfuscation, legitimate network tools and credentials to exfiltrate data through DNS requests, making it harder to detect the malicious activity among normal network traffic.
When data is stored on Züs, it is distributed across multiple data centers, making it extremely difficult for an attacker to compromise the entire system. In a zero-trust network, the attacker would need to target each server’s operator individually and successfully execute a phishing attack to install malware—an impractical and highly complex task.
The 2016 Democratic National Committee (DNC) Email Phishing Attack involved sending phishing emails to members of the DNC, including campaign chairman John Podesta, which looked like a Google security alert, urging him to change his password. When he clicked on it, he was directed to a fake Google login page, which allowed the attackers to gain access and leak data.
If an app uses Züs for storage, it can also leverage Züs's split-key based two-factor authentication (2FA) for customer logins. Traditional 2FA is often avoided because it adds friction to the login process. With Züs, 2FA can be always-on—operating silently, seamlessly, and without user interruption. This frictionless security can also be extended to all file operations, offering a level of continuous authentication that doesn’t exist in today’s systems.
In mid-July 2024, Azure Multi-Factor Authentication (MFA) experienced a significant outage caused by a configuration issue.
If an app uses Züs storage along with its split-key-based 2FA, users are no longer dependent on a centralized authentication server and are protected from potential outages. Authentication occurs locally through Bluetooth Low Energy (BLE) between devices in close proximity to the user. Unlike traditional 2FA, which is limited to login events, Züs 2FA is always-on and secures all file operations—offering a level of continuous, decentralized authentication that doesn’t exist today.
In March, several French state services were targeted by a cyberattack over a day with over 300 web domains and 177,000 IP addresses impacted, including severe disruptions to major public service websites.
If websites host their JavaScript bundles and assets on Züs as the primary storage and use shareable links to render the site, then even if the original instance is taken down by a DDoS attack, a new instance can be instantly spun up in another data center to continue serving the site seamlessly. This makes the attack significantly harder to sustain, as the attacker would now need to locate and target the new infrastructure—a far more complex task.