Private, Fast & Secure DataHub
Breachproof Security. ACID compliant. Zero-knowledge. Zero API and Egress Costs.
Discover Why Blimp is the Only True Secure Cloud Storage.
Discover Why Blimp is the Only True Secure Cloud Storage.
Recently discovered pitfalls of Encryption Encryption ≠ Security 1, 2

Attackers can inject malicious keys into the encryption process

Attackers can force protocol downgrades, preventing encryption

Allows malicious servers to intercept & replace encryption keys

Files are renamed or relocated maliciously, leading to data loss

Attackers can modify or replace data chunks without detection

Attackers insert malicious files & folders leading to data breach

Attackers modify encrypted files undetected, corrupting data

Embedding passwords in shared links are intercepted
The master key is anchored on the blockchain, ensuring a unique and verifiable ID.
Enterprise securely stores master key in zVault, generating Split Keys for operational use.
Split Key is in all Clients and Servers making the master private key impenetrable to internal and external breach.
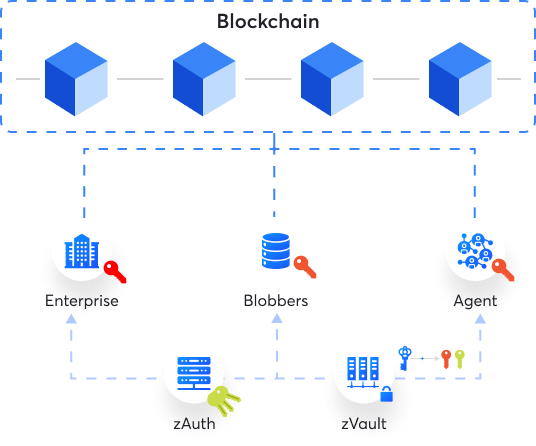
Data contract between Client and Servers is recorded on the blockchain.
& Public Encrypted Sharing
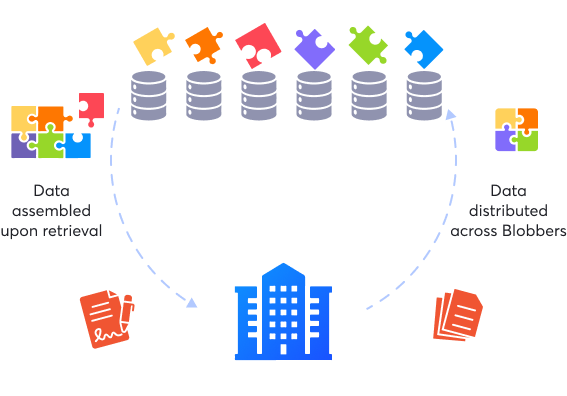
Data is encoded with user defined redundancy and distributed among Blobbers.
Data privacy and availability is not compromised with the hack of servers.
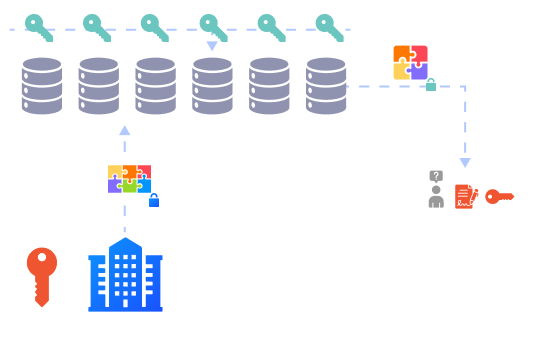
Enterprise generates Proxy Key when sharing encrypted data based on Client's Private Key and Recipient's Public Key. Proxy Key is distributed to servers.
Blobbers use the Proxy Key to re-encrypt the data and can only be decrypted by the Recipient's Private Key.
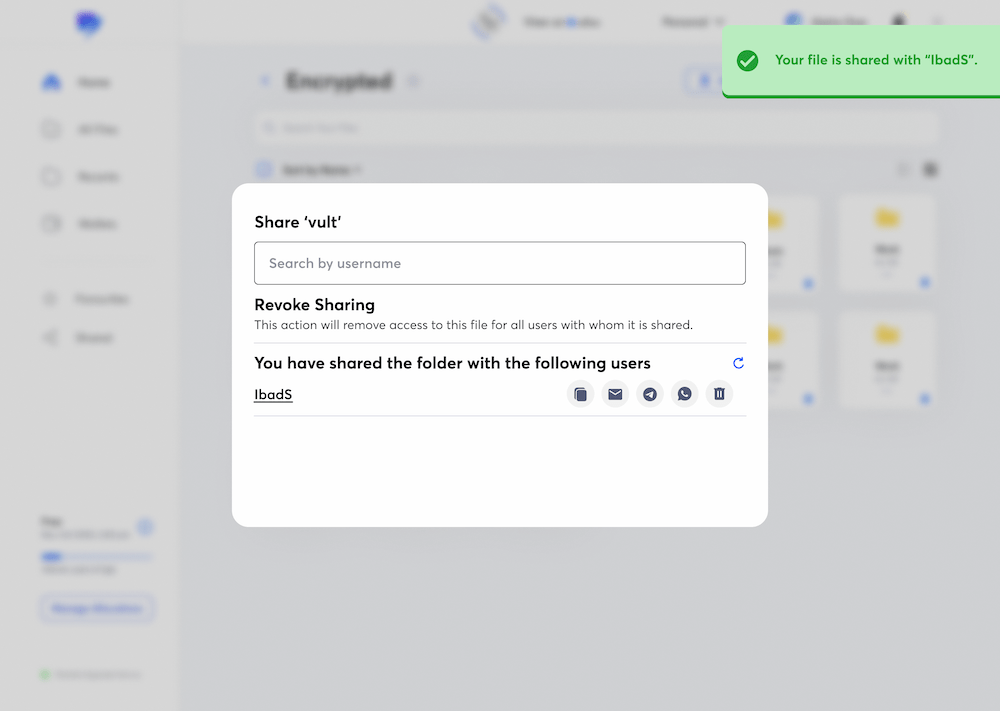
Easily share an authentication link publicly for convenience—no secure connection required.
1.5/3 = 50% Less Disk Usage
3 times data expansion

1.5 times data expansion

Data is fragmented across multiple servers, each secured with a unique Split Key, ensuring that even if a server is hacked, neither the private key nor the data is compromised.
Effortlessly share encrypted files and folders with customers and teams using Proxy Keys. Boost productivity with Shared Drives and enable ultra-secure collaboration through Split-Key technology
Users own and control the Private Key, assuming full GDPR liability, freeing the platform and infrastructure from responsibility.
Users own their keys, control data storage locations, and can seamlessly add or replace providers with automatic synchronization.
You control availability by configuring parity servers, selecting brand, performance, and location. Effortlessly add or replace servers with automatic synchronization, while always-on repair and add server features ensures 100% dynamic availability.
Enhance availability and content distribution by adding providers, or optimize performance by replacing them
Data is fragmented across multiple servers, each secured with a unique Split Key, ensuring that even if a server is hacked, neither the private key nor the data is compromised.
Encrypted Private Sharing uses distributed Proxy Key technology to keep your data encrypted when sharing to any 3rd party.
Encrypt files so that no one can view them except for you.
A Proxy Key, created from the owner’s and recipient’s public keys, is distributed across decentralized servers for added security and to prevent single point of breach.
Files can only be decrypted by the recipient with their Private Key from the public auth link shared by the data owner
Data owner decides who can open their files from the shared public link and can cancel access at any time.
Use shared drives for customers, partners, and teams to securely collaborate effortlessly, without the need for file transfers.
Store data on Züs to have unparalleled security, availability, and privacy.
Build on Züs to protect against internal breach and exceed GDPR compliance.
Use Züs SDK, a no-code integration, for your hot backup and disaster recovery solution — with unmatched security and privacy